Protect and Accelerate on Your Multi-Cloud Edge
AxisNow provides security, performance, and connectivity for your websites, applications, and APIs — all running on infrastructure you control.

The AxisNow Connectivity Cloud
Powering Safer, Faster, Smarter Applications.
Build Your Edge Network
Run a command line deployment in Linux, or deploy in bulk through a cloud provider.
Use the Admin API or IaC to automate deployment in any environment.
Cluster deployment maximizes performance, reliability, and scalability.

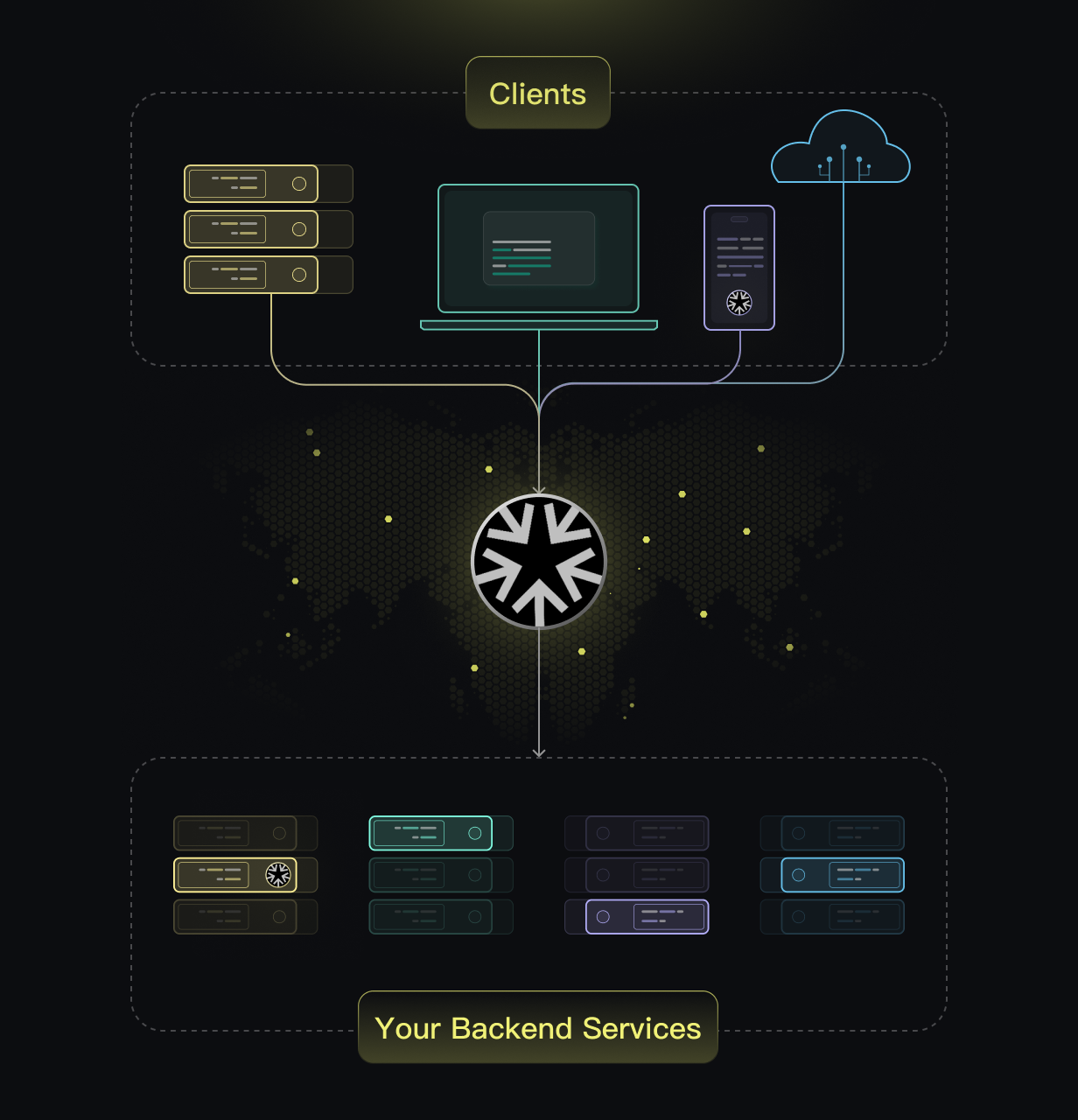
Connect Your Clients & Services
General HTTPS/TCP application proxy – from your first domain to your millionth.
Expand native/mobile application client/agent to achieve powerful security, performance, and reliability.
Based on WireGuard, securely connect your remote network.
Function Extension and Fine-Grained Control
Use a series of plugins to upgrade your edge to: DNS Traffic Routing Management, Automatic HTTPS, Rate Limiting, Bot Challenge, Cache, WAF, Identity-Aware Proxy, API Gateway, Performance and Availability Monitoring, and more.
Use a DSL rules engine for fine-grained traffic control.


Get Deep Visibility
Entity analysis and monitoring, including but not limited to edge, resources, devices, plugins, and other entity objects.
Global traffic analysis, end-to-end tracing analysis of usage, performance, and error metrics.
Original log recording and retrieval, tenant operation auditing, view on the dashboard or transfer to your SIEM.
Automation Deployment and Maintenance

Deploy with Terraform (WIP)
Integrates into existing IaC tooling to reduce time to rollout across multiple environments including multi-cloud deployments.

Deploy with Our API
AxisNow's API-first design easily integrates with your stack, that allows you to programmatically deploy and maintain.





Build a Best-In-Class Ecosystem
Leverage out-of-the-box integrations with major Cloud service provider (CSPs), Credential providers (CPs) , SIEMs, DNS providers, and more.
Why Our Customers Choose AxisNow
AxisNow provides the best of both worlds. A hosted control plane and a self-hosted data plane.
Self-Hosted Edge
A self-hosted proxy that enables flexibility and privacy over your data.
Simple and Powerful
Scalable with many features, but easy to deploy and maintain.
Production Ready
Ensure providing the necessary speed, scalability, and reliability for production.
Your Security and DevOps will both love the edge platform
From free to production to enterprise level.
